ISO 27001:2013
ISO 27001:2013
Information security is a hot topic these days;no company or organisation is completely immune to cyber attacks or data breaches. Moreover, the European General Data Protection Regulation (GDPR), or General Data Protection Regulation (AVG), imposes a series of obligations to better protect European citizens' data.-when processing their data.
Sound information security is therefore a must for today's businesses. To better control these risks, set up an information security management system based on the ISO 27001:2013 standard.
What is ISO 27001
ISO 27001 is the global standard for information security. The important basis for certification against this standard is the implementation of an information security management system (ISMS) to include process-based information security. For this, the ISO 27001 standard describes with a set of requirements how to set up, evaluate and continuously improve an effective ISMS. The goal: to ensure the confidentiality, availability and integrity of all data within your organisation.
- Confidentiality - Only authorised persons are given access to the information.
- Integrity - The information is accurate, complete and correct.
- Availability - The information is accessible at appropriate times and in a timely manner.
The ISO27001 certificate is a must-have quality label for many companies in a technology- and data-driven world. Customers, suppliers, employees... can trust that as an organisation you have taken measures against information security risks and that you treat personal data with care, because this has been independently established.
Often, companies have all hardware and software regulated, but information security is not just about IT security (e.g. firewalls, anti-virus, etc.) - it is also about controlling processes, legal protection, controlling human resources, physical protection, etc. Much of an ISO 27001 management system is therefore about setting organisational guidelines needed to prevent information security breaches.
ISO 27001:2013
ISO 27001 is an international standard published by the International Organisation for Standardisation (ISO), developed on the basis of the British standard BS 7799-2. That standards document - as is the case with other management standards - has been reviewed regularly over the years by an expert committee. The committee then decides whether to revise or withdraw the standard.
The first revision of the standard was published in 2005, and the most recent version of this standard was published in 2013 where the structure was changed to the High Level Structure (HLS) to work under the same uniform basic structure.
The latest version in Dutch is NEN-EN-ISO/IEC 27001:2013 Management systems for information security - Requirements. 'NBN' stands for the Bureau for Standardisation, a Belgian government body responsible for developing standards in Belgium. The 'EN' suffix in turn refers to the European publication by CEN-CENELEC.. The year is the version of the standard.
Why ISO 27001 certification?
With ISO 27001 certification, you take the extra step when it comes to information security. The certificate gives your customers the assurance that you are serious about information security, setting you apart from competitors and reducing security risks.
Everyone wants to be sure that their data is in safe hands with your organisation. The ISO 27001 certificate gives you an image as a reliable party that handles personal data carefully and complies with laws and regulations. With this, you lay the foundation for a strong relationship of trust.
There are increasing laws, regulations and contractual requirements around information security - such as the GDPR. The good news is that the ISO 27001 standard provides a perfect methodology for complying with these. So by maintaining your ISMS, you also ensure that you are legally compliant.
More and more customers are demanding that partners they work with have their information security in order. The ISO 27001 certificate gives them that assurance. This not only contributes to your image, it can also generate commercial opportunities and new tenders.
Loss of reputation and customers can lead to serious financial damage. With a certified ISMS, you reduce the risk of information being misused, and stay alert to security risks at all times by systematically detecting and specifically addressing vulnerabilities.
The content of ISO 27001
ISO 27001 - like most ISO standards - is drafted according to the Harmonised Structure (HS) principal.This means that these standards have a common core text and the same structure. This ensures that topics covered in each standard are always addressed in the same place (chapter & paragraph).
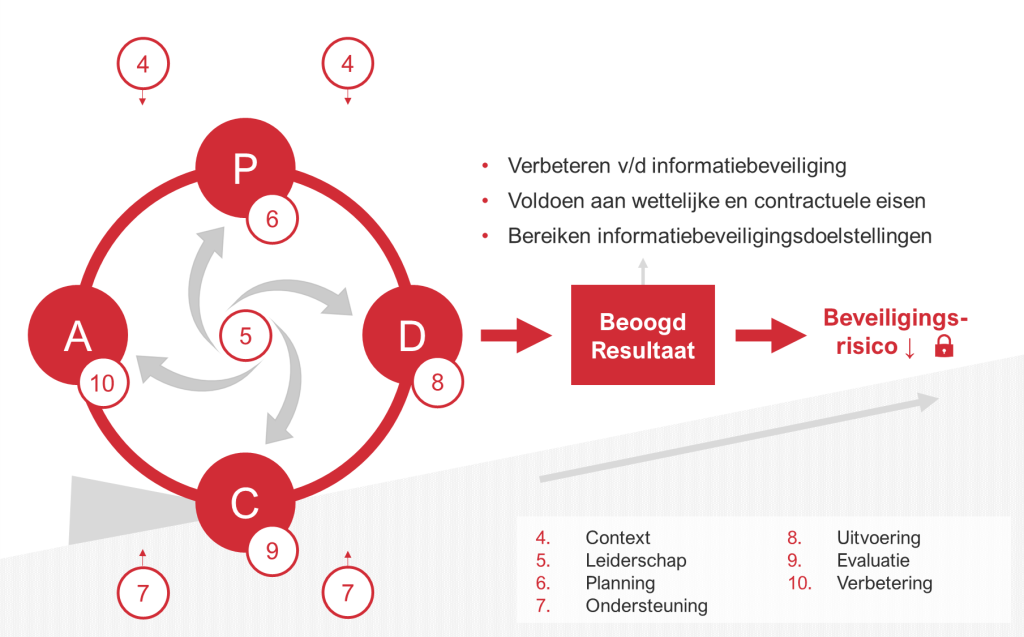
The standard consists of 11 chapters, which are shown below. The first four chapters (0 to 3) contain general explanations, while chapters 4 to 10 describe the core of the standard, i.e. the standard requirements.
| Chapter 0: Introduction | Chapter 6: Planning |
| Chapter 1: Scope | Chapter 7: Support |
| Chapter 2: Normative references | Chapter 8: Implementation |
| Chapter 3: Definitions | Chapter 9: Evaluation |
| Chapter 4: Context of the organisation | Chapter 10: Improvement |
| Chapter 5: Leadership |
Who is ISO 27001 intended for?
ISO 27001 is useful for any organisation that wants to demonstrate that they are serious about information security.After all, information is everywhere. Think of customer data, data from a production system, data from the R&D lab or financial reporting. As a result, an ISO 27001 ISMS can be implemented in an ICT company, but also in banks, insurers, government agencies, healthcare institutions, non-profit organisations and other companies that have or process confidential information.
Information security is not only about IT security (e.g. firewalls, anti-virus, etc.) - it is also about controlling processes, implementing organisational measures, ... So it is certainly not only the IT manager, but the whole organisation, that can benefit from an ISO 27001 certificate.
The ISO 27000 series
Although ISO 27001 is the only certifiable standard within the 27000 series, it can be useful to apply the management standard in combination with other standards from the same family. The standards in the ISO 27000 series help manage the security of, for example, financial information, intellectual property, employee data or information entrusted by third parties. It consists of the following standards and guidelines, among others:
- ISO 27000 – ‘Information technology – Security techniques – Information security management systems – Overview and vocabulary’
- ISO 27002 – ‘Information technology – Security techniques – Code of practice for information security controls’
- ISO 27018 – ‘Information technology – Security techniques – Code of practice for protection of personal identifiable information (PII) in public clouds acting as PII processors’
- ISO 27701 – ‘Security techniques – Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management – Requirements and guidelines’
ISO 27002 offers an in-depth look at the ISO 27001 standard, so to speak. This is because this standard details the measures you can take to meet the standard requirements of ISO 27001. Whereas ISO 27001 is a short and concise document, ISO 27002 offers more information and details.